1 Wireless Hacks, 2nd Edition by Rob Flickenger, Roger Weeks
- Author: oreilly.com
- Published Date: 10/07/2022
- Review: 4.83 (974 vote)
- Summary: But Wi-Fi is intended primarily for Internet data and connecting computers, while Bluetooth is used to communicate between a wide variety of devices. Where WiFi
- Matching search results: First, make sure you have a supported Bluetooth adapter. You used to be able to find a reasonably current list of BlueZ-supported hardware at http://www.holtmann.org/linux/bluetooth/devices.html. However, as of March 2005, this information has been …
- Source: 🔗
2 Billions of Android devices have been exposed to hacks through Bluetooth
- Author: phonearena.com
- Published Date: 09/12/2022
- Review: 4.78 (324 vote)
- Summary: · The issue affects over one billion people who own any of the vulnerable Android and Windows devices, running compromised Bluetooth firmware. So
- Matching search results: First, make sure you have a supported Bluetooth adapter. You used to be able to find a reasonably current list of BlueZ-supported hardware at http://www.holtmann.org/linux/bluetooth/devices.html. However, as of March 2005, this information has been …
- Source: 🔗
3 New Bug Hacks Android Devices Via Bluetooth
- Author: pcmag.com
- Published Date: 01/27/2022
- Review: 4.47 (440 vote)
- Summary: · Hackers physically close enough could exploit the activated Bluetooth connection on a phone to run malicious computer code, according to
- Matching search results: First, make sure you have a supported Bluetooth adapter. You used to be able to find a reasonably current list of BlueZ-supported hardware at http://www.holtmann.org/linux/bluetooth/devices.html. However, as of March 2005, this information has been …
- Source: 🔗
4 Critical Bluetooth flaw exposes your phone to malware – heres how to patch it
- Author: komando.com
- Published Date: 03/25/2022
- Review: 4.33 (365 vote)
- Summary: · And now, a new security flaw has been discovered in Bluetooth on older Android phones that can let a hacker waltz right in to steal your
- Matching search results: However, operating system vulnerabilities are a much bigger deal. They can affect millions of users around the world if not addressed properly. And now, a new security flaw has been discovered in Bluetooth on older Android phones that can let a …
- Source: 🔗
5 How hackers are targeting your phone through Bluetooth
- Author: pandasecurity.com
- Published Date: 02/26/2022
- Review: 4.02 (508 vote)
- Summary: · Keeping Bluetooth enabled on your devices allows hackers to break into them and access your data. This is how, and some tips to stay safe
- Matching search results: However, operating system vulnerabilities are a much bigger deal. They can affect millions of users around the world if not addressed properly. And now, a new security flaw has been discovered in Bluetooth on older Android phones that can let a …
- Source: 🔗
6 How to hack a phone: 7 common attack methods explained
- Author: csoonline.com
- Published Date: 01/29/2022
- Review: 3.85 (524 vote)
- Summary: · Mobile security often beats PCs, but users can still be fooled and smartphones can still be hacked. Here’s what you need to watch for
- Matching search results: “Most apps interface with the operating system and other applications on what are essentially API calls,” he explains. “The kernels for iOS and Android are so vastly different from anything that would resemble their Unix base that shared exploits …
- Source: 🔗
7 Hacking Cell Phones via Bluetooth Tools under Linux
- Author: linuxjournal.com
- Published Date: 12/21/2021
- Review: 3.66 (309 vote)
- Summary: · So, instead of purchasing a specialized USB cable, I decided to connect to it using a standard USB Bluetooth dongle. The dongle should work with
- Matching search results: “Most apps interface with the operating system and other applications on what are essentially API calls,” he explains. “The kernels for iOS and Android are so vastly different from anything that would resemble their Unix base that shared exploits …
- Source: 🔗
8 Researchers found another way to hack Android cellphones via Bluetooth
- Author: cyberscoop.com
- Published Date: 06/30/2022
- Review: 3.52 (405 vote)
- Summary: · Attackers looking to steal sensitive information from Android cellphones only need to target their Bluetooth protocols, according to
- Matching search results: “Most apps interface with the operating system and other applications on what are essentially API calls,” he explains. “The kernels for iOS and Android are so vastly different from anything that would resemble their Unix base that shared exploits …
- Source: 🔗
9 Alert! Windows 10 PC & Android Phones Are In Danger Of Bluetooth Hack Data Theft: Research
- Author: republicworld.com
- Published Date: 01/04/2022
- Review: 3.19 (265 vote)
- Summary: · A study conducted by Singapore University reports that a group of bugs and vulnerabilities which are being commonly called BrakTooh can
- Matching search results: “Most apps interface with the operating system and other applications on what are essentially API calls,” he explains. “The kernels for iOS and Android are so vastly different from anything that would resemble their Unix base that shared exploits …
- Source: 🔗
10 How Do Hackers Hack Phones and How Can I Prevent It?
- Author: mcafee.com
- Published Date: 12/16/2021
- Review: 3.09 (200 vote)
- Summary: · The threat of having your phone hacked has become a common fear. The truth is that it is possible to hack any phone. With the advancement of
- Matching search results: These are a classic form of attack. In fact, hackers have leveled them at our computers for years now too. Phishing is where hackers impersonate a company or trusted individual to get access to your accounts or personal info or both. And these …
- Source: 🔗
11 How to Hack Bluetooth Devices: 5 Common Vulnerabilities
- Author: hackernoon.com
- Published Date: 03/25/2022
- Review: 2.96 (188 vote)
- Summary: · This article discusses the five common vulnerabilities (BlueBorne, Bluesnarfing, Bluejacking, BIAS & Bluebugging) that allow hackers to hack
- Matching search results: Most people leave their Bluetooth enabled all the time when they should only really enable it when needed. Of course, this is much easier said than done, and therefore unlikely to be followed. To showcase some of the dangers of careless Bluetooth …
- Source: 🔗
12 How to use headphones or Bluetooth to hack and take control of any Android device

- Author: securitynewspaper.com
- Published Date: 06/17/2022
- Review: 2.82 (167 vote)
- Summary: · There are vulnerabilities in this communication that can be exploited by using peripheral devices controlled by threat actors. Typically, a
- Matching search results: A recent research published by vulnerability testing specialists from Purdue University details a new exploit that abuses some Android operating system smartphones through the use of malicious peripheral devices (specifically through Bluetooth and …
- Source: 🔗
13 Bluetooth Hacking, Part 1: Getting Started with Bluetooth
- Author: hackers-arise.com
- Published Date: 09/02/2022
- Review: 2.67 (126 vote)
- Summary: In this series, we will be focused on hacking mobile devices, tablets, and phones as they are the most fertile ground for hackers. The ability to hack Bluetooth
- Matching search results: A recent research published by vulnerability testing specialists from Purdue University details a new exploit that abuses some Android operating system smartphones through the use of malicious peripheral devices (specifically through Bluetooth and …
- Source: 🔗
14 Can my phone be easily hacked?
- Author: computerworld.com
- Published Date: 04/29/2022
- Review: 2.69 (110 vote)
- Summary: · What vulnerabilities does Bluetooth present and what are some easy ways to help secure your smartphone?
- Matching search results: Of course one should always keep the phone at close hand and install software to help locate the phone and wipe it remotely if necessary. But have you ever contemplated that the convenience of connecting to your phone with your ear bud or in-auto …
- Source: 🔗
15 How To Know Your Phone Is Hacked? A Basic Insight In 2022
- Author: jigsawacademy.com
- Published Date: 11/22/2021
- Review: 2.55 (179 vote)
- Summary: How do I keep my smartphone secure? Additional Tips to Protect Your Phone from Hackers. WHAT IS PHONE HACK? Phone hack refers to any method by which someone
- Matching search results: The instructions for resetting an android phone can depend on the manufacturer. You can visit your Android phone manufacturer’s website to know the steps to reset your android phone. Most android phones have the option of resetting in the setting …
- Source: 🔗
16 How to Know If Your Phone Has Been Hacked
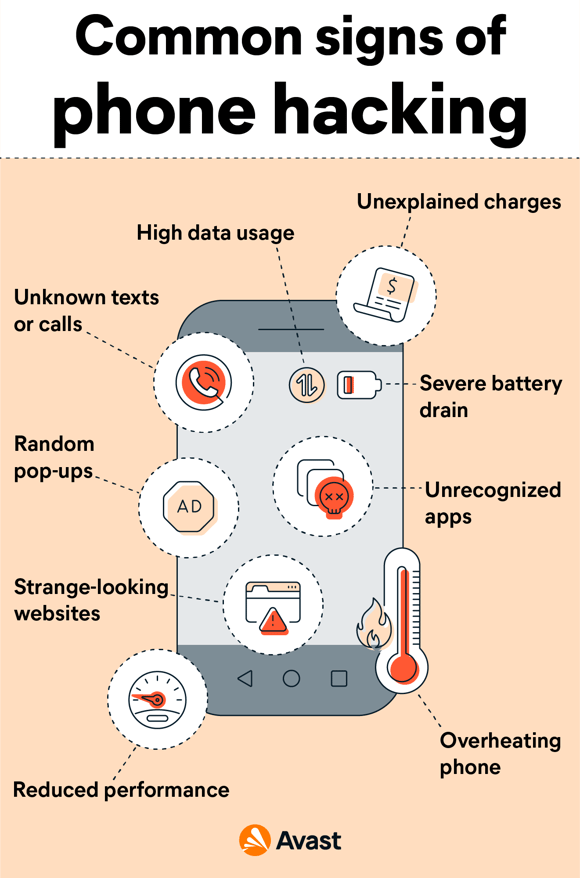
- Author: avast.com
- Published Date: 12/12/2021
- Review: 2.46 (151 vote)
- Summary: · Is your phone acting strangely? It could be a hacker. Unfortunately, phone hacking is on the rise — affecting device performance and leaving
- Matching search results: If your phone bill is higher than usual, you could be incurring unexpected charges from unwanted apps running on your phone and spiking your data use. Fleeceware apps stuff your bill with excess charges, and if someone has remote access to your …
- Source: 🔗
17 Mobile Hacking – How to Hack an Android Phone?

- Author: codecnetworks.com
- Published Date: 08/31/2022
- Review: 2.36 (86 vote)
- Summary: · In this period of time mobile has taken over desktops and computers as mobile phones are now they enable the user to access email, browse the
- Matching search results: As mobile has provided technological advances by having the option to send messages, email and have the feature of download applications via the internet, hackers misuse these advances for malicious purposes like sending malformed apk files or click …
- Source: 🔗
18 New Bluetooth vulnerability can hack a phone in 10 seconds
- Author: techcrunch.com
- Published Date: 06/24/2022
- Review: 2.12 (129 vote)
- Summary: · The attack can allow access to computers and phones, as well as IoT devices. “Armis believes many more vulnerabilities await discovery in the
- Matching search results: “Armis believes many more vulnerabilities await discovery in the various platforms using Bluetooth. These vulnerabilities are fully operational, and can be successfully exploited, as demonstrated in our research. The BlueBorne attack vector can be …
- Source: 🔗
19 Hackers Can Take Over Billions of Android and Linux Devices via Bluetooth
- Author: fortune.com
- Published Date: 01/12/2022
- Review: 2.16 (95 vote)
- Summary: · Hackers can wirelessly take over billions of Google Android, Microsoft Windows, Linux, and Apple iOS devices vulnerable to Bluetooth hacks
- Matching search results: “Customers who have Windows Update enabled and applied the security updates, are protected automatically,” a Microsoft (MSFT) spokesperson tells Fortune. “We updated to protect customers as soon as possible, but as a responsible industry partner, we …
- Source: 🔗
20 How to Prevent Phone Hacking and Protect Your Cell Phone

- Author: webroot.com
- Published Date: 05/30/2022
- Review: 1.99 (192 vote)
- Summary: Phone hacking used to be a celebrity issue, but with so much personal information stored on our smartphones now, it is a serious security threat to us all
- Matching search results: Remember—if the thought of hacking has you tossing and turning at night, you can just turn the phone off, remove the battery and hide it under your pillow for some sweet lithium-ion induced dreams. Or, you can double down on securing your mobile …
- Source: 🔗
