1 Experts fear LockBit spread after ransomware builder leaked
- Author: therecord.media
- Published Date: 01/23/2022
- Review: 4.89 (831 vote)
- Summary: · A toolkit to create DIY versions of the LockBit ransomware has … that the builder works and allows anyone to create their own ransomware
- Matching search results: Even though it is customizable, the encryptor still changes the victim wallpaper to say “Lockbit Black,” according to Hammond, who noted that more skilled operators may try to change that. More low-tier groups, meanwhile, may even want the …
- Source: 🔗
2 How to Create Your Own Ransomware
- Author: bluent.net
- Published Date: 05/13/2022
- Review: 4.75 (576 vote)
- Summary: · For creating custom ransomware or malware you don’t need to be a full-fledged coder, no coding skills and hacking skills is required
- Matching search results: Well, the payments are automated, which means that ransom is first sent to the developers where they deduct 20% of the amount and return the rest 80% to your Bitcoin address specified. Once the victim sends the ransom, a decryption key is generated …
- Source: 🔗
3 How to create your own ransomware
- Author: cybervow.com
- Published Date: 05/24/2022
- Review: 4.51 (228 vote)
- Summary: · Ransomware is a type of malware that encrypts files on the victim’s computer and then demands a ransom be paid in order for the user to
- Matching search results: The creators at Atom claim that their ransomware employs a quick and powerful encryption technique, supports several languages, and won’t be detected by antivirus software. You can choose which folders to infect, which files to infect, which …
- Source: 🔗
4 How To Create Your Own Ransomware? What is a ransomware creator? Full Guide
- Author: globallyindia.com
- Published Date: 04/19/2022
- Review: 4.24 (264 vote)
- Summary: · How to Protect Yourself from Ransomware Threat? How to create your own Free Ransomware; The Hidden Tear Free Ransomware Kit; The key feature for
- Matching search results: The currently undetectable version of ransomware can be modified and implemented accordingly, as it contains every feature a cybercriminal can expect from modern malware. Sen describes his Ransomware as “a ransomware-like file crypter sample which …
- Source: 🔗
5 How To Create Your Own Ransomware
- Author: searchis.com
- Published Date: 08/09/2022
- Review: 4.11 (436 vote)
- Summary: · How do Hackers Create Ransomware? What Code is Ransomware Written in; How Do Hackers Install Ransomware? What is a Ransomware Creator? Why Do
- Matching search results: By creating my Ransomware, this software is very much helpful. It has made it easy for me to mitigate the risk of falling into the trap of Ransomware after guiding me on how to install it on my device. Using the Ransomware creator is easy because …
- Source: 🔗
6 How to Create Your Own Ransomware Password
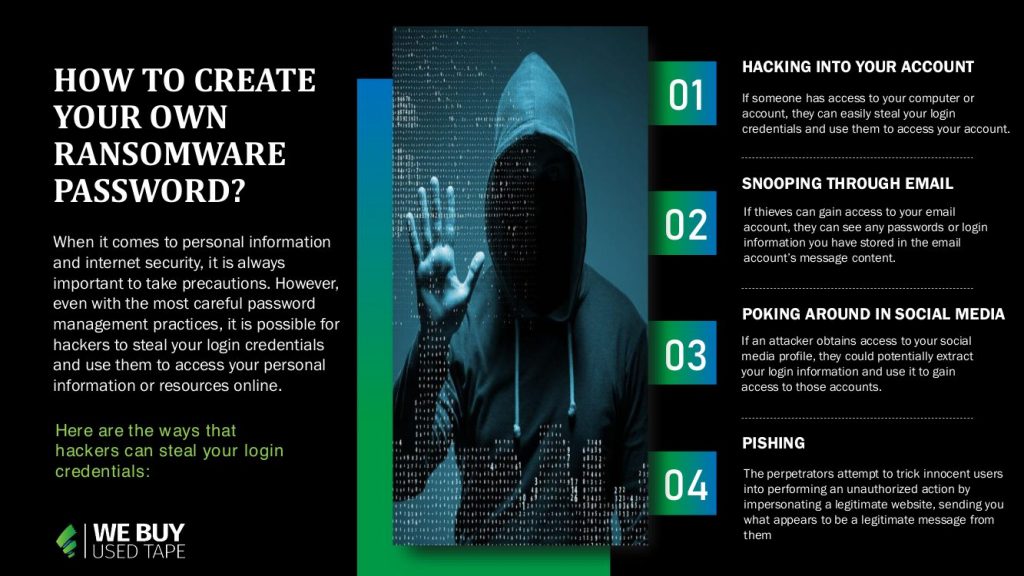
- Author: dtc1.com
- Published Date: 01/16/2022
- Review: 3.85 (497 vote)
- Summary: · Creating a ransomware password can help in protecting against an unwanted attack. Heres how you can get your own ransomware password
- Matching search results: When it comes to personal information and internet security, it is always important to take precautions. However, even with the most careful password management practices, it is possible for hackers to steal your login credentials and use them to …
- Source: 🔗
7 Ransomware explained: How it works and how to remove it
- Author: csoonline.com
- Published Date: 04/07/2022
- Review: 3.79 (219 vote)
- Summary: That won’t stop a malware attack, but it can make the damage caused by one much less significant. Ransomware removal. If your computer has been infected with
- Matching search results: But here’s the important thing to keep in mind: while walking through these steps can remove the malware from your computer and restore it to your control, it won’t decrypt your files. Their transformation into unreadability has already happened, …
- Source: 🔗
8 How to create your own ransomware
- Author: enterprise.comodo.com
- Published Date: 02/12/2022
- Review: 3.42 (240 vote)
- Summary: · In an aim to better protect and mitigate the risk to yourself from malware, it can be helpful to know how to create your own ransomware
- Matching search results: Some ransomware creators can also produce mobile ransomware for those who’d want to cast a wider net. Swindling made-easy for any average Joe. Unfortunately, such service is available to the public. Albeit, not everyone could do it or else more …
- Source: 🔗
9 Ransomware Attack – What is it and How Does it Work? – Check Point
- Author: checkpoint.com
- Published Date: 08/14/2022
- Review: 3.32 (350 vote)
- Summary: Dozens of ransomware variants exist, each with its own unique … Once file encryption is complete, the ransomware is prepared to make a ransom demand
- Matching search results: Lapsus$ is a South American ransomware gang that has been linked to cyberattacks on some high-profile targets. The cyber gang is known for extortion, threatening the release of sensitive information, if demands by its victims aren’t made. The group …
- Source: 🔗
10 Ransomware as a Service: Unravelling this Ecosystem
- Author: spiceworks.com
- Published Date: 04/10/2022
- Review: 3.01 (352 vote)
- Summary: · Keeping track of ransomware groups, their attack methods and their … To begin with, threat actors would create and deploy their own
- Matching search results: IABs are the go-betweens that help streamline a ransomware operation giving the threat actor an entry point to focus on to begin their attack. Regardless of the organization’s location, size, sector, or yearly revenue, IABs are likely to know an …
- Source: 🔗
11 Build Your Own Ransomware (Project Root) | Behind Enemy Lines Part 2
- Author: sentinelone.com
- Published Date: 04/22/2022
- Review: 2.99 (184 vote)
- Summary: · In Part 2 of our Ransomware As A Service (RaaS) series, we look at Project Root’s offline builder & how threat actors can easily customize
- Matching search results: At the time, their .onion TOR-based portal was advertising both a “standard” and “Pro” version of the service. The major differentiator between the two being anyone who purchases the “Pro” version gets their own copy of the source code, along with a …
- Source: 🔗
12 Ransomware – Definition – Trend Micro
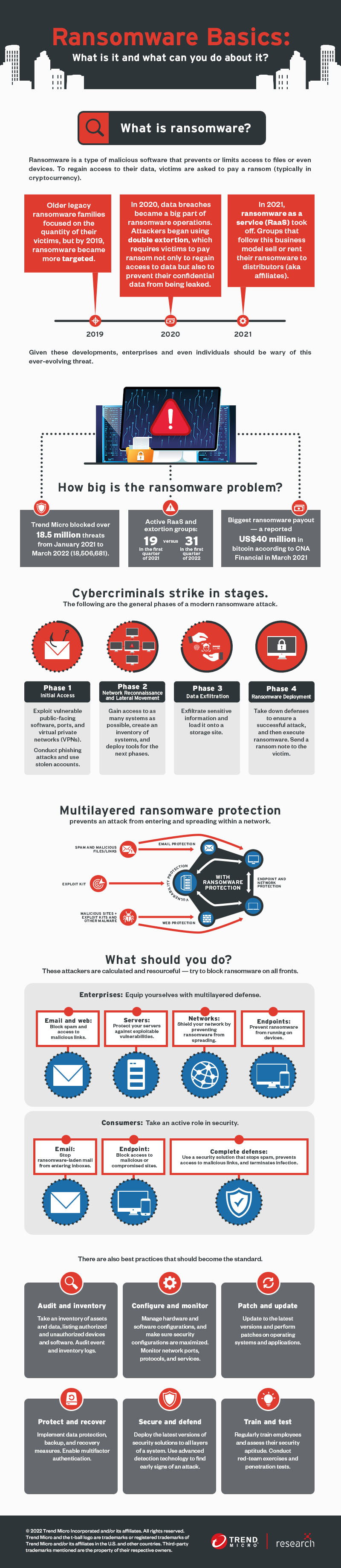
- Author: trendmicro.com
- Published Date: 03/01/2022
- Review: 2.84 (183 vote)
- Summary: Create a culture of security and equip personnel with adequate knowledge on ransomware and … Once enlisted, affiliates can then launch their own attacks
- Matching search results: Users might encounter this threat through a variety of means. Ransomware can be downloaded onto systems when unwitting users visit malicious or compromised websites. It can also arrive as a payload that is either dropped or downloaded by other …
- Source: 🔗
13 What is Ransomware? | How to Protect Against … – Malwarebytes

- Author: malwarebytes.com
- Published Date: 05/17/2022
- Review: 2.73 (115 vote)
- Summary: Ransomware is a form of malware that locks the user out of their files or their device, then demands … Make sure your device is protected from ransomware
- Matching search results: In 2020, yet another new family of ransomware named Egregor came on the scene. It’s thought to be somewhat of a successor to the Maze ransomware family, as many of the cybercriminals who worked with Maze changed over to Egregor. Similar to Maze, …
- Source: 🔗
